
What Does Weak Security Mean on Wi-Fi?
What Does Weak Security Mean on Wi-Fi? – Let’s Review
‘What does weak security mean on Wi-Fi?’ This Wi-Fi security notice should not generate alarm, but it should direct your attention to finding a solution as soon as possible.
Because your phone or laptop detects that the Wi-Fi network is using an obsolete, “weaker” security protocol that is not entirely secure, your Wi-Fi displays the phrase “weak security.”
Wireless security protects our data and privacy by preventing illegal access to our wireless devices. Evil individuals on the internet can acquire access to our privacy and data due to a Wi-Fi router’s lack of security.
These individuals are sophisticated enough to hack into our virtual world, which contains significantly more information than we maintain in physical possession. They can access any number of devices linked to a network with inadequate Wi-Fi security.
An ineffective security standard that employs a weak password can readily be circumvented or cracked. These criminals are using essential software tools and equipment to get access to the internet.
‘What does weak security mean on Wi-Fi?’ – so what is the significance of this message as it relates to some devices, such as iPhones? The ability to detect poorly setup routers has been included in the most recent iOS 14 release.
As a result, numerous users have reported receiving an iPhone message claiming that their Wi-Fi is not secure due to “poor security” while connecting to an older router with insufficient protection.
Should you be worried?
Not necessarily. The inadequate Wi-Fi security indication shows that the network to which you are connected does not use the most up-to-date, entirely secure protocols or passwords.
It does not suggest that the network has been hacked or infiltrated. In reality, you may continue to use low-security Wi-Fi (the internet will still work), but it is not recommended owing to obvious security concerns.
Why is it Critical to Protect your Wireless Connection?
You most likely did not prioritize network security while selecting a Wi-Fi router.
After all, when it comes to home wireless internet, most of us are more concerned with data transfer speeds and the router’s range.
But now is the moment to reconsider. Network security must be considered since a Wi-Fi station is a gateway for devices to connect to the internet.
Almost everyone nowadays possesses at least one internet-connected device. As the number of these devices grows by the day, we must protect our wireless connections and tools to reduce the risk of privacy invasions.
‘What does weak security mean on Wi-Fi’ entail for your network?’ – as it relates to the question, why is it essential to secure your Wi-Fi connection?
* Entities or data sharks commonly target these devices to get personal information. They steal identities and put personal and financial information at risk to get unnoticed access to our data.
* Intruders may get access to our devices and listen to, record, read, transmit audio and video, and read, create, and send communications.
* You’re in significant danger if your wireless network isn’t secure. Intruders can intercept any data you send or receive, view your files, get unwanted access to your internet connection, and drain your bandwidth.
As a result, anytime you consider ‘what does weak security means on W-iFi’, you should be aware that the issues discussed above may occur with weak security Wi-Fi.
This type of behavior may be avoided by implementing an enhanced security standard and making a few adjustments to your router configuration.
What Security Type is My Wi-Fi?
So, now that we have discussed ‘what does weak security means on Wi-Fi,’ it’s critical to ask, ‘what security type is my Wi-Fi?’

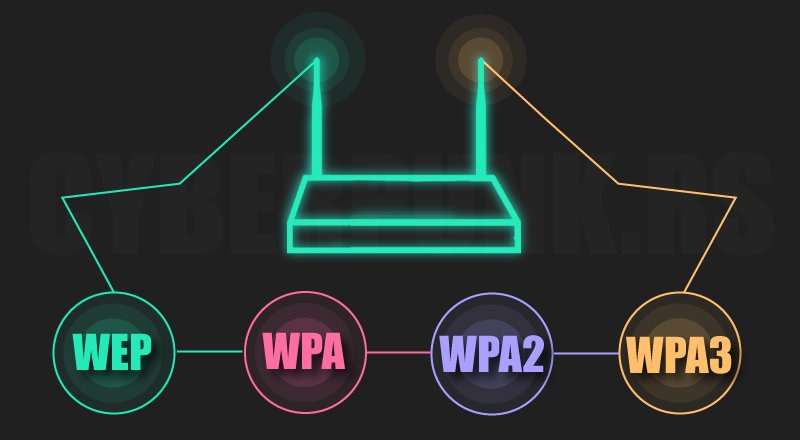
Four different Wi-Fi encryption methods have been created to solve insufficient Wi-Fi security: WEP, WPA, WPA2, and WPA3.
* The initial security protocol was WEP, which stood for Wired Equivalent Privacy. WEP was first implemented in 1997 as part of the IEEE 802.11 standard protocol to provide data confidentiality for wireless networks. It is essentially the oldest and least effective Wi-Fi encryption technology available.
* In 2003, WPA supplanted WEP. WPA stands for Wi-Fi Protected Access, and it was developed as an interim standard following the deprecation of WEP and in preparation for the more secure WPA2.
* Wi-Fi Protected Access II (WPA2) was adopted in 2004 and included key elements of the IEEE 802.11i standard. WPA2 outperforms WPA by improving the authentication and encryption mechanisms used by the latter. It is widely used in modern Wi-Fi encryption.
* In 2018, WPA3 (Wi-Fi Protected Access III) was released to solve WPA2’s flaws and vulnerabilities, such as its susceptibility to brute-force attacks and key reinstallation attacks (KRACK).
The most current Wi-Fi encryption protocol is WPA3. It also supports Easy Connect for IoT devices.
This latest security update will not only make Wi-Fi connections more secure, but it will also safeguard you from security risks caused by you.
Begin by thinking about how WPA3 will safeguard you at home. It will significantly limit the damage caused by your poor password selections.
WPA2 has a fundamental flaw: hackers may guess your password via an offline dictionary attack.
Without being on the same network, an attacker may guess your password as many times as possible, fast cycling through the dictionary.
WPA3 will defend against dictionary attacks with a new key exchange technique.
The other advantage comes in case your password is still compromised.
WPA3 now supports forward secrecy, which implies that any communication that occurred before to prior to an outsider gaining access will be encrypted. They can even decrypt WPA2 signals that are no longer in use.
To encourage wider use, WPA3 is fully compatible with WPA2 devices.
It should be noted, however, that the WP3 protocol may only be utilized with routers produced in 2019 or after.
How Do I Know What Security Type I’m Using
You may be able to identify the security type by utilizing the Wi-Fi settings on your mobile device. To determine the kind of encryption:
1. Open your mobile device’s Settings app.
2. Open the Wi-Fi connection settings.
3. Look for your wireless network on the list of networks.
4. To examine the network configuration, click the network name or the information button.
5. Examine the network settings to determine the security type.
If your mobile device’s security type is not indicated, you may be able to detect it by modifying the settings on your wireless router.
Step 1: Access the router’s settings.
Because different Wi-Fi devices have different configurations, how you access your router settings depends on the brand and manufacturer of your device.
The majority of routers use 192.168.0.1 or 192.168.1.1 as their IP address. You may access your router’s settings page by typing the IP address into your browser’s hostname area. You may also access the settings page by putting the hostname into your browser (for example, tplinkwifi.net).
Step 2: Find the security options.
This varies depending on your router but check for the Wireless Security option. So, look for terms like encryption or security.
Step 3: Change the security standard (if Needed)
Once you’ve located the security choices, pick WPA2 (AES) or WPA3 (AES) as your security standard; remember to select “WPA2 alone” rather than “WPA/WPA2.”
Depending on your router, you may need to pick “WPA/WPA2” first, followed by WPA2 from a second option.
Don’t be alarmed if you don’t see WPA3 as an option; many Wi-Fi routers do not support it. Choose “WPA3/WPA2-Personal” if your router supports WPA3 to guarantee that your devices may connect to your Wi-Fi.
Step 4: Put the changes into action
Finally, “Save” or “Apply” the changes depending on the option on your router’s settings page.
‘What does weak security mean on Wi-Fi?’ You now know how to strengthen the security of your Wi-Fi network. With a few simple actions, you can make your Wi-Fi more secure.
Wi-Fi Security Recommendations
Almost every family member utilizes a laptop, PC, smartphone, or tablet to connect to the internet.
A minor flaw in your Wi-Fi network can give hackers access to virtually all Wi-Fi devices. Access might lead to problems with bank accounts, credit card information, child safety, and so on.
The following recommendations are designed to aid you in protecting your Wi-Fi network from illegal access.
1. Modify the name of your wireless network.
The first step in wirelessly protecting your network is to change the SSID (service set identifier). The SSID of a network identifies it.
Many manufacturers give all of their wireless routers a default SSID. In most cases, it is the name of the firm.
The SSID of each network that broadcasts is publicly recognized when a wirelessly connected computer searches for and displays neighboring wireless networks.
This raises the likelihood of a hacker breaching your network.
Change the network’s SSID to something that does not disclose any personal information to prevent hackers from jeopardizing your wireless security.
2. Network access restrictions
Did you know that you may prevent specific devices from accessing your Wi-Fi?
You can allow or disallow particular devices from joining your Wi-Fi network.
Every smartphone, tablet, laptop, desktop, and printer is given a unique identification number known as a Media Access Control (MAC) address.
You may analyze, filter, and deny or accept the connection from your router’s homepage.
3. Change the default passwords
The bulk of network equipment, including wireless access points, comes with pre-configured default administrator passwords to make configuration easier. Because default passwords are widely available online, they provide little protection.
Increasing the difficulty of guessing default passwords makes it more difficult for attackers to get access to a device. The first line of protection for your device’s security is to use and often change complex passwords.
4. Make use of the latest recent WPA network encryption.
As we described in the last section, there are numerous types of Wi-Fi security that you may use for your network. Please make it a habit always to use the most recent version available.
If your router only provides Wired Equivalent Privacy (WEP) security, it should be replaced because it is probably out of date in other respects.
WPA is adequate; WPA2 is significantly superior and perhaps the most recent version that most routers can support today, and it is sufficient. Although WPA3 is the most current version available, it is not supported by all routers. If possible, make the transition to improve your Wi-Fi security.
As mentioned in the last section, you may alter the Wi-Fi encryption in your router settings, which is also the page where you can change your password.
5. Make sure your router is up to date.
Before installing a new router or upgrading an old one, check the manufacturer’s website to see whether a more recent version of the software is available for download.

To ensure you obtain the most recent version, sign up for updates and register your router with the manufacturer. If you bought your router from an Internet Service Provider (ISP) like Verizon or Comcast, find out if they provide automatic updates.
The majority of routers allow you to create a separate guest network with its own name and password. t’s a prudent security measure for a couple of purposes:
1. Having a second login guarantees that your primary Wi-Fi network password is known by fewer people.
2. If a guest accidentally has spyware on their phone or tablet, it will not get onto your primary network or your devices.
7. Ensure that you have a solid firewall.
A “firewall” is software that protects computers against malicious invasions.
Wireless routers usually include built-in firewalls; nonetheless, the firewall is routinely turned off. Check that the wireless router’s firewall is enabled.
If your router lacks a firewall, install a reliable firewall solution on your device to monitor for unauthorized access and boost your wireless security.
8. Keep commercial-grade antivirus software on hand at all times.
Install and keep your virus definitions current. with commercial-grade antivirus software. Many antivirus products now include tools for detecting and protecting against spyware and adware.
Sophos Home Premium, developed by Sophos Limited, a British company specializing in digital security, is my preferred antivirus tool.
Sophos Home Premium monitors application activity on your home computer network with the same sophisticated artificial intelligence used in commercial antivirus security solutions for large enterprises experiencing regular ransomware threats.
Sophos now provides the same degree of security for home PCs as it does for roughly 300 million commercial devices worldwide.
Visit this website to discover more about Sopho’s commercial-grade antivirus protection for your home.
9. When utilizing mobile devices, use the utmost caution.
Some mobile apps may be able to connect to your home network.
A mobile hotspot on your smartphone, for example, looks to be safe, but don’t forget to remotely turn off the network afterwards. Mobile device use necessitates the use of a password.
Always use a password that is at least 20 characters long and includes alphanumeric and symbol characters.
Also, once you’ve finished using the app, log out. Also, make sure your phone has a secure password. or multi-factor authentication (MFA) activated. These step guards against misuse of the phone and app.
10. Use a Virtual Private Network (VPN)
A VPN acts as a barrier to safeguard your online activities. Installing a VPN on all of your internet-capable devices lets you browse the internet safely when at home or on the move.
Wi-Fi may be available at coffee shops, restaurants, clubs, and school campuses depending on where you are.
There is no way to determine the level of security on these networks.
A man-in-the-middle attack, in which an attacker intercepts data on an unprotected network, might be used to eavesdrop on your connection and take your data.
These assaults pose a significant risk to persons who do their work at home. According to statistics, 80 percent of remote workers operate mostly from home, with 27 percent working from a coffee shop as a secondary location.
A VPN’s primary role is to encrypt your connection, allowing you to access the internet safely even when using public hotspots.
At this juncture, you should have a solid grip on ‘what does weak security mean on Wi-Fi? It is a problem with your Wi-Fi connection that may jeopardize your security.
The Wi-Fi router can redirect network traffic. It also monitors all of your devices, including tablets and laptop PCs.
Anyone who gains access has access to all of your devices and data. Weak Wi-Fi security is the gateway via which such devices may be hacked.
As a result, safeguarding your router is essential. The approaches and solutions listed above are simple to implement and will invalidate the nagging question, ‘What does weak security mean on Wi-Fi?’
Our Top VPN Provider
A trustworthy VPN service creates a safe, encrypted tunnel through which web traffic can travel. Nobody can look through the tunnel, access your online data, or determine your actual IP address and location.
NordVPN is the top VPN if you want to feel safe when using public Wi-Fi. Access personal or professional data securely, encrypt your internet connection and hide your browser history and online identity.
Do you want to keep all of your devices safe?
Do you use Windows at work, Mac OS at home, and Linux occasionally? On all platforms, you will have online privacy and security.
NordVPN also provides Windows, macOS, iOS, Android, Linux, and Android TV apps. Encrypted proxy plugins are also available for Chrome, Firefox, and Edge.
The best part is that a single NordVPN subscription allows you to encrypt up to six devices simultaneously. It is the best VPN provider for all of your devices, with 14 million subscribers worldwide.
Do you want to be able to access the internet fast and dependably from any location?
Buffering is the ultimate buzzkill, so using a poor internet connection to broadcast or download anything would be out.
There’s no need to be apprehensive; what distinguishes NordVPN from other VPNs is its unrivaled mix of unbreakable security, lightning-fast connection speed, and boundless capacity.
Choose from over 5400 NordVPN servers in 60 countries and enjoy the fastest VPN experience available anywhere globally, from the United Kingdom to Australia or Canada.
Do you want to avoid advertising, trackers, and malware?
Threat Protection, NordVPN’s newest feature, takes your cybersecurity to the next level.
It does not require you to connect to a VPN server to function. If you enable Threat Protection in the settings, your surfing will be safer and smoother indefinitely.
Don’t be concerned about visiting a dangerous website, downloading malware, or dealing with trackers and annoying advertisements. Threat Protection will identify and eliminate cyber attacks before they cause any significant damage to your device or data.
Click here for more information about NordVPN, our top choice, including its award-winning features and security and its 30-day money-back guarantee.
The Post: What does weak security mean on Wi-Fi? was first seen on https://websecurityhome.com
This Post is Brought to You By:













Ah, the classic “weak security” alert – it’s a modern-day equivalent of the “check engine” light for our digital lives, isn’t it? It’s like your Wi-Fi network is raising a little flag, waving it frantically at you like a lifeguard spotting a potential swimmer in distress. “Hey you! Yeah, you! Let’s keep that data safe, shall we?”
You’ve painted such a vivid picture with that analogy. It’s true; just like that “check engine” light can spark a moment of concern, weak security alerts can really make us pause and think about how exposed we might be. Our Wi-Fi networks are often set to default settings, which isn’t a great starting point for security.
You make a really good point about those “check engine” lights. It’s interesting how something so small can trigger a big reaction, both in driving and in our online lives. Weak security alerts often feel like that dashboard warning, urging us to take a moment and evaluate our vulnerabilities. There’s something to be said about how we tend to ignore those signals until something goes wrong, and then it’s a mad scramble to fix it.
You’ve captured the essence perfectly. That “check engine” light is such a striking metaphor for how we approach both our vehicles and our digital lives. In many ways, it reflects our tendency to prioritize immediate conveniences over long-term upkeep. Just as ignoring that light can lead to serious car troubles, brushing off weak security alerts can open the door to larger issues down the line.
You raise an interesting point about those signals and how they often fly under our radar until we face a real issue. It’s fascinating to think about how both the dashboard light and weak security alerts serve as reminders to stay vigilant, yet so many of us tend to brush them aside.
You’re spot on about those “check engine” lights and their parallels to our vulnerabilities in the digital space. It’s so easy to overlook those signals, whether they’re on our dashboards or popping up on our screens.
I appreciate that perspective. It’s interesting how that “check engine” light serves as a metaphor for so many aspects of our lives, isn’t it? Just like cars need regular checks, we often overlook the security of our digital spaces until something prompts us to act.
You bring up an important point about how we tend to overlook things until they become a problem. That “check engine” light isn’t just about our cars; it speaks to a larger issue in how we manage our lives, especially in the digital realm. Many of us push aside the nagging worry about our online security, waiting for a crisis to force our hand.
It’s so true how that “check engine” light can reflect our own oversight in different areas of life. I find it fascinating how we often wait for a warning before we prioritize maintenance, whether it’s our vehicles, our health, or even our digital security.
You’ve captured a really interesting perspective on the “weak security” alert. It’s true—just like that ominous “check engine” light, a weak security notification stirs a certain level of unease. It serves as a wake-up call, even if it often comes too late for many who overlook their digital surroundings.
You’ve really hit the nail on the head with that comparison to the “check engine” light. It’s fascinating how both serve as alerts that something may be off, yet often we tend to ignore them until it’s too late. With our increasing reliance on technology, having these weak security notifications loom over us feels like that ever-present anxiety that comes with modern life.
That perspective on security alerts really resonates; speaking of navigating risks, I recently came across an article that dives into the world of a local handyman in Winnetka, shedding light on tips and experiences that might help us all feel a bit more secure in our homes.
‘A Handyman in Winnetka, Los Angeles – Revealed Everything’
https://cable13.com/a-handyman-in-winnetka-los-angeles-revealed-everything/.
It’s interesting how we often wait for that “check engine” light to turn into something much more serious before we take action, whether it’s with our cars or our personal security. I think the parallels between physical and digital safety highlight a deeper cultural tendency to only react when faced with a pressing issue. It reminds me of how easy it is to overlook small signs of trouble in various facets of life, from health to home safety, until they escalate.
You’ve hit on something that really resonates. It’s fascinating how we often go through life with blinders on, tuning out those small indicators that something might be amiss until it reaches a critical point. You think you have plenty of time before you need to change the oil or check your smoke detectors, but then—bam—something big comes crashing down, whether that’s a car breakdown or an emergency at home.
It’s so true, isn’t it? Life has a way of reminding us to pay attention to the small things, especially when we tend to overlook them. Those little indicators are often the universe’s way of giving us a nudge, but sometimes we’re too wrapped up in our routines to notice. I’ve had a couple of moments where I thought I had all the time in the world to take care of maintenance—like that time I pushed off a dentist appointment until I had a sudden toothache. It really drives home the importance of taking proactive steps in all areas of our lives, whether it’s health, home, or even our relationships.
You’ve hit on something that really resonates. It’s interesting to reflect on how life often pulls us in so many directions that we overlook those small indicators. I’ve experienced that feeling of having everything under control, only to find out later that I was neglecting something crucial. A couple of months ago, I put off getting my car’s routine maintenance done. I kept thinking I’d get to it next week, and then one day, the engine light came on, and I was suddenly facing a much bigger issue than if I’d just taken the time earlier.
I appreciate your thoughts on the “check engine” light analogy. It’s interesting how we often react to the warnings our cars give us, yet when it comes to digital security alerts, we tend to sweep them under the rug. This tendency to ignore these signs until they escalate into bigger issues feels especially poignant in our tech-driven lives, where everything is interconnected and vulnerabilities can easily compound.
You’re spot on about that “check engine” light analogy. It’s so easy to dismiss those warnings in both our cars and with technology until we find ourselves in a bind. It definitely reflects a larger trend in how we manage risks, don’t you think? Our daily lives are filled with alerts and notifications, which can often feel overwhelming or even lead to that anxiety you mentioned. It’s like we’re constantly juggling between staying informed and not letting ourselves spiral into a state of worry over things we can’t control.
I completely agree with your comparison to the “check engine” light. It’s that subtle yet persistent reminder that we often dismiss until something goes seriously wrong. It’s a bit alarming when you think about how ingrained that habit is, not just with our cars but in our daily lives—whether it’s mental health signals or security notifications, we frequently sideline those alerts.
It’s interesting how you brought up that comparison to the “check engine” light. It really reflects the broader challenge we face in our tech-driven lives. So many of us zoom past those warning signs without taking a moment to pause and assess what’s really going on. It’s a bit of a paradox, isn’t it? We rely on these systems to make our lives easier, yet they often come with a load of anxiety because we know we might be ignoring something important.
You’ve hit the nail on the head with the paradox of modern technology. It really does feel like we’re on this treadmill, constantly moving forward without taking a moment to consider the signals around us. I often catch myself doing the same—rushing through my day, relying on my devices, and then realizing later that I missed some important ‘check engine’ moments, whether that’s in my personal life or my mental well-being.
That’s a thought-provoking point, and it reminds me of how cultivating energy-saving habits can be a practical way to tune into our daily lives and heed those subtle signs of overconsumption.
‘Create Energy-Saving Habits’
https://cable13.com/create-energy-saving-habits/.
I appreciate your thoughts on the “check engine” light analogy; it’s a reminder of how easy it is to overlook those small signals in our lives, whether they’re related to personal safety or technology. It’s interesting how we often prioritize immediate concerns over those less obvious indicators.
You’ve brought up an interesting analogy with the “check engine” light. I think it’s fascinating how both situations reveal our relationship with alerts, whether for our vehicles or our digital security. This uneasy feeling often stems from a larger theme in our lives: the struggle to balance convenience with safety.
You’ve brought up an interesting analogy with the “check engine” light. It really does make you think about how we react to different kinds of alerts in our lives. There’s this instinctive push and pull between wanting to ignore or silence them for convenience and understanding that they often signal something important. I recently read about how our increasing reliance on technology has created a sort of “alert fatigue,” especially in the context of cybersecurity. With so many notifications pinging our devices, it’s easy to feel overwhelmed and dismiss them without a second thought.
You’ve captured that analogy perfectly. It’s true that these notifications often feel like the digital equivalent of a lifeguard can’t just keep an eye on things but also needs to make sure everyone understands the potential dangers. The “weak security” alert acts like a friendly nudge—something that should ideally prompt us to reassess our digital habits and security measures.
Speaking of keeping our data safe, I just read something about a private browser that really gets the job done—it’s like the trusty lifeguard for your online adventures.
‘Best Private Browser For PCs – Session Splitter Wins’
https://cable13.com/best-private-browser-for-pcs-session-splitter-wins/.
You’ve captured that feeling perfectly. It’s interesting how we often overlook the digital equivalent of a “check engine” light until it’s too late. Like the lifeguard you mentioned, our Wi-Fi networks are kind of like those overprotective friends who want to ensure we’re making good choices. It makes me think about how we often take our online security for granted, almost like the way some of us neglect our physical health until something goes wrong.
This topic of Wi-Fi security couldn’t be more pressing in our increasingly connected world! The notion of “weak security” on Wi-Fi makes me think about how often we take internet safety for granted, assuming that just because we’re home or in a public place, our data is safe. However, as you pointed out, using outdated security protocols can leave us vulnerable to cyber threats that many of us might not fully comprehend.
You’ve touched on an important aspect of Wi-Fi security that many people overlook. It’s true that in our daily lives, we often operate under the assumption that our data is secure when we’re connected to our home networks or even in public spaces. The reality is, though, that we live in an era where cyber threats are evolving constantly, and weak security protocols can serve as an open invitation for malicious actors.
It’s interesting how often we overlook the importance of Wi-Fi security in our daily lives. I remember when I first got a notification about weak security on my home network; it really made me stop and think about how exposed my devices were. I ended up updating my router settings and changing my password to something more complex. It’s a small step, but I feel like I’ve added a layer of protection that’s definitely worth it.
You make a really important point about Wi-Fi security. It’s so easy to take it for granted until something prompts us to take action. I had a similar experience when I realized just how many devices rely on my network. Between smart home devices, laptops, and phones, it was daunting to think about how they could be vulnerable.
It’s so true how a simple notification can open our eyes to something we often take for granted. We tend to think of security as something far out of reach or only relevant to tech experts, but it’s really about making small, manageable changes that anyone can do.
It’s great to hear about your experience with Wi-Fi security. Many of us don’t really think about it until we receive that little wake-up call. Changing your password and updating the router settings is such a significant move in taking control of your online safety.